Optimize your asset management with our Unified Asset Management Services! Boost efficiency and reduce costs today.
ExploreWith our Cyber Security Consultant
In order to effectively handle your company's cybersecurity, it is crucial to identify and locate your assets. With the evolving cyber landscape, understanding your vulnerable internet-facing assets requires a comprehensive assessment.
Unified asset management is an essential component of a proactive and comprehensive security strategy. It enables your security team to maintain a real-time inventory of all IT assets within your organization, providing unified cyber insights.
Unified asset management architecture based on cybersecurity principles provides a robust solution for safeguarding an organization's assets and data against cyber threats. By adopting unified asset management, businesses can achieve a centralized view of all enterprise systems, enabling administrators to assess their state and make informed decisions to enhance security measures. This proactive approach empowers organizations to swiftly implement necessary protections, eliminating the need for reactive measures or costly retrofits post-attack. The benefits of unified asset management architecture based on cybersecurity principles encompass:
Cybersecurity is not a sideline
In the dynamic realm of cybersecurity, businesses that embrace a strong asset management strategy can confidently introduce new IT services and resources without compromising security or encountering unnecessary obstacles. By gaining a deep understanding of the diverse threats and vulnerabilities specific to your organization, you can effectively manage upcoming changes while maintaining control and ensuring a secure environment.
Security visibility
Cybersecurity asset management enables security teams to effectively investigate the root cause of an attack and devise appropriate remediation strategies. Instead of starting from scratch to assess resource deployments and settings when investigating breaches or vulnerabilities, teams can rely on an easily accessible and updated record. This streamlined process empowers teams to quickly refer to the relevant information, facilitating more efficient and targeted incident response.
Proactive action
Unified cybersecurity asset management enables proactive threat detection and swift response by continuously monitoring the IT estate. It offers comprehensive visibility into the environment, allowing early risk identification and faster action when needed.
Mindfire can help you protect your OT assets from cyber threats. We have the skills, technology and resources to provide an organisation-wide solution covering all aspects of your security needs. The most common OT devices that need full visibility to minimise cyber risks include:
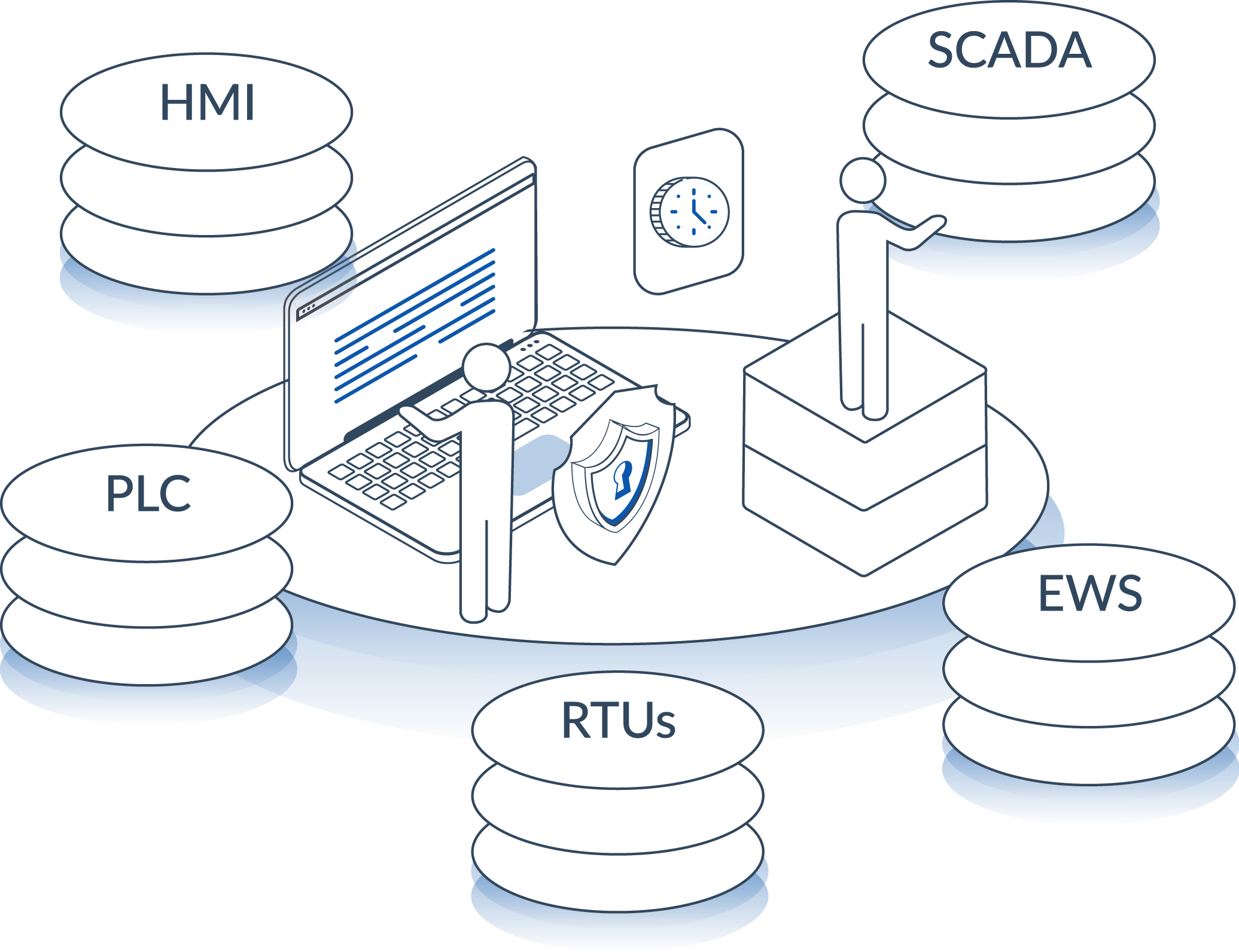
Mindfire is your trusted partner for cybersecurity asset management. Our services provide a real-time view of all your assets, from devices and applications to sensitive data.
Asset categorization
Our cyber professionals use the industry's best asset inventory tools that provide businesses with a complete, up-to-date list of all their assets. We keep track of everything happening in the network and determine which assets are internet-facing and where they are located. So whether you're starting from scratch or want to improve your current asset management system, Mindfire can help you get there quickly
Security control protection
When you hire us, we'll work closely with your security team to ensure that all critical assets are properly protected. Our cyber experts uncover gaps in security policies and vulnerabilities and help you implement the most effective measures to protect your assets.
Automated policy management
Security policies are essential to protect your business from attack. But often, implementing and maintaining a comprehensive security policy is a time-consuming and cumbersome task. That's where we come in! We can help you automate applying security policies to harden your assets against attack. This will save you time and money, allowing you to focus on other, more important tasks.
Enhanced resource information
Our asset management solution helps you gain rich context from internal and external sources to uncover security risks. With our data-driven approach, you can identify potential threats early and take steps to mitigate them.
In today's fast-paced, ever-changing enterprise, having a unified inventory and management system is more important than ever. This system should be able to keep track of all the devices and apps in use by different parts of the organisation, as well as their current configuration and status. In addition, this system should be able to update itself automatically with new software versions or changes made to existing software applications. And that's exactly what Mindfire's asset inventory solution does. We put an end to manually updating software inventories, replacing outdated and error-prone methods with a real-time inventory that is constantly up to date. This way, you can be sure that the devices and apps in use by your organisation are always properly managed and under control.
Unified asset inventory
We use our unique data collection and analysis capabilities to provide you with a unified view of all your assets. This includes services, devices and applications. We automatically clean up and combine conflicting or duplicate data, which helps you quickly find problems in asset protection, compliance management, network security, system performance monitoring and other areas.
Constant inventory control
Mindfire can help you assess the criticality of your assets and identify potential cyber-risks. You can use this data to make informed decisions about cybersecurity and compliance measures.
Mindfire is a trusted leader in cybersecurity, offering specialized expertise in asset management architecture based solutions. Our team excels in policy automation, data analysis, and threat detection to help you achieve your organization's cybersecurity goals. Partnering with top-tier cybersecurity providers, we deliver a unified asset management approach that covers all aspects of your security program.
But wait, there's more! Our certified staff possess a diverse range of cybersecurity skills, ensuring we have the precise knowledge and expertise needed to safeguard your valuable assets. If you're seeking a robust asset management solution that significantly enhances your security posture, don't hesitate to get in touch with Mindfire today!
If you are looking for reliable and efficient solutions to enhance your business operations, Mindfire is the perfect partner for you. Contact us today to learn more about our services and how we can help you achieve your goals. Whether you need Cyber Security Services, Managed Security Services (MSS), Consulting Services, Cyber Risk Management Services, Cloud Services, Digital Services, or Digital Transformation, our team of experts is here to assist you every step of the way. Don't hesitate to get in touch with us and take your business to the next level with Mindfire.
